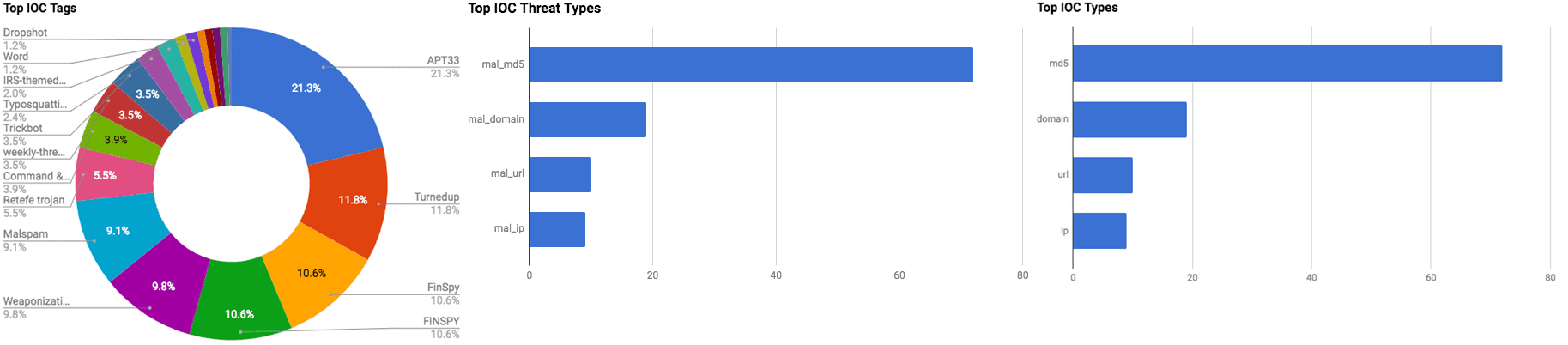

The intelligence in this week's iteration discuss the following threats: APT, Banking trojan, Data breach, Malspam, Mobile, Ransomware, Spear phishing, Typosquatting, and Vulnerability. The IOCs related to these stories are attached to the WTB and can be used to check your logs for potential malicious activity.
Trending Threats
Oracle Patches Apache Vulnerabilities (September 25, 2017)
The U.S. Computer Emergency Readiness Team (CERT) has issued a statement concerning Apache Struts 2 vulnerabilities. The U.S. CERT has confirmed that Oracle has released security updates to address Apache Struts 2 vulnerabilities located in multiple products. A threat actor could remotely exploit these vulnerabilities to take control of a system running vulnerable versions.
Recommendation: The U.S. CERT advises Oracle customers to view the company's Security Alert Advisroy located at "http://www.oracle.com/technetwork/security-advisory/alert-cve-2017-9805-3889403.html". The security updated should be applied as soon as possible if it has not been already.
Tags: Vulnerability, Apache Struts 2
A Song of Ice and Ransomware: Game of Thrones Reference in Locky Phishing (September 22, 2017)
The threat actors behind the "Locky" ransomware have been identified to be conducting a new malspam campaign themed after the television show "Game of Thrones," according to PhishMe researchers. The Game of Thrones' references were identified in Visual Basic script variables that were contained in the emails' malicious attachments.
Recommendation: Educate your employees on the risks of opening attachments from unknown senders. Anti-spam and antivirus applications provided from trusted vendors should also be employed. Emails that are received from unknown senders should be carefully avoided, and attachments from such senders should not be opened.
Tags: Malspam, Locky
Technical Update and Ongoing Analysis of the APT Security Incident (September 21, 2017)
Avast Threat Labs researchers have released information regarding Command and Control (C2) communication a second-stage backdoor that was identified in their product "CCleaner." Piriform, the company that created CCleaner and was acquired by Avast, confirmed on September 18, 2017, that certain versions of CCleaner and "CCleaner Cloud" were subject to a supply chain attack and then distributed malware to users. Researchers discovered that the C2 for the malware was running since the end of July, but the data gathering did not begin until August 11. The attacks are believed to have been conducted by the Advance Persistent Threat (APT) group "APT17."
Recommendation: It is crucial that your company ensure that servers are always running the most current software version. In addition, your company should have policies in place in regards to the proper configurations needed for your servers in order to conduct your business needs safely. Furthermore, always practice Defense in Depth (do not rely on single security mechanisms - security measures should be layered, redundant, and failsafe).
Tags: Vulnerability, CCleaner
Retefe Banking Trojan Leverages EternalBlue Exploit in Swiss Campaigns (September 21, 2017)
Proofpoint researchers have discovered that the "Retefe" trojan has added the "EternalBlue" exploit to its malicious capabilities. Retefe primarily targets Austria, Japan, Sweden, and Switzerland. Recent observations have revealed that Retefe is being distributed via malspam with Microsoft Office attachments. The attachments contain OLE objects and images that attempt to trick the recipient into following a link on the document attachment, which executes a PowerShell command to download a payload.
Recommendation: Always be on high alert while reading email, in particular when it has attachments, attempts to redirect to a URL, comes with an urgent label, or uses poor grammar. Use anti-spam and antivirus protection, and avoid opening email from untrusted or unverified senders.
Tags: Malspam, Banking trojan, Retefe
New FinFisher Surveillance Campaigns: Internet Providers Involved? (September 21, 2017)
The spyware called "FinFisher," known for its use by governments and their agencies, has been observed to be active in the wild and with new updates, according to ESET researchers. FinFisher is capable of capturing images via webcam, audio via microphone, as well stealing files and keylogging functionalities. Researchers have found use of man-in-the-middle (MITM) attacks in the wild and they believe that the malicious actor is operating at the Internet Service Provider (ISP) level.
Recommendation: One way of mitigating against these types of attacks is to move away from HTTP and instead, use HTTPS. Websites should ensure they are using HTTP Strict Transport Security (HSTS) to prevent user's connections from being downgraded. In the case an upstream actor is performing a TLS Man In The Middle (MITM, HTTP Public Key Pinning (HPKP) can be used detect any tampering and switches of certificates. Application developers can also sign the binaries using a public key crypto. This gives the users the capability of verifying that both the downloaded file is not corrupted and that it is identical to the one published by the developer.
Tags: Spyware, FinFisher
Fake IRS Notice Delivers Customized Spying Tool (September 21, 2017)
Malwarebytes researchers have discovered a malspam campaign in which actors are impersonating documents from the U.S. Internal Revenue Service (IRS). Specifically, the document purports to be a "CP200" which is a notice of underreported income, typically used when an individual has entered information incorrectly on a previous return. The emails come with a malicious Microsoft Office attachment containing an OLE object that will infect recipients with a custom Remote Access Trojan (RAT) when clicked on.
Recommendation: Impersonation of government entities is a commonly used tactic by threat actors in malspam and phishing campaigns. It is important to educate your employees on the risks of opening attachments from unknown senders. Anti-spam and antivirus applications provided from trusted vendors should also be employed. Emails that are received from unknown senders should be carefully avoided, and attachments from such senders should not be opened.
Tags: Malspam, IRS-themed, RAT
ATP33 Targets Aerospace and Energy Sectors and has Ties to Destructive Malware (September 20, 2017)
FireEye researchers have published their findings on a new Advanced Persistent Threat (APT) group dubbed, "APT33." The group is believed to be based in Iran and has been active since at least 2013. APT33 has primarily targeted the aviation sector in the Saudi Arabia, and the U.S., as well as the petrochemical industry in South Korea. However, other countries and business sectors were also identified to have been targeted. APT33 primarily uses spear phishing emails as the initial infection vector that attempt to trick the recipient into following a link to a malicious HTML application. The group also typosquatts domains that may appear familiar to their targets at first glance to augment their spear phishing tactics.
Recommendation: Defense in depth (layering of security mechanisms, redundancy, fail safe defense processes) is the best way to ensure safety from APTs, including a focus on both network and host based security. Prevention and detection capabilities should also be in place. Furthermore, all employees should be educated on the risks of spear phishing, and how to identify such attempts.
Tags: APT, APT33, Spear phishing, Typosquatting
SEC Reveals It Was Hacked, Information May Have Been Used for Illegal Stock Trades (September 20, 2017)
The U.S. Security Exchange Commission (SEC) has announced that they were compromised by threat actors in 2016. The SEC confirmed in a public statement that they detected the breach in 2016 and discovered that it may have provided the basis for insider trading in August 2017. The system that was compromised was used for storing documents that were filed by publicly-traded companies. The SEC has stated that the unknown actors may have been able to use the unauthorized data access to make illegal profits in the U.S. stock market.
Recommendation: Always practice Defense in Depth (do not rely on single security mechanisms - security measures should be layered, redundant, and failsafe).
Tags: Breach, SEC
The Shark CryptoMix Ransomware Variant Smells Blood in the Water (September 20, 2017)
A new variant of the "CryptoMix" ransomware has been identified adding a ".shark" extension to encrypted files, according to researcher Lawrence Abrams. Researchers state that the encryption functionality of this variant is the same as previous iterations, but this variant has new contact emails for payment communication. This variant contains 11 public RSA-1024 encryption keys, of which one is used to encrypt the AES key that is used to encrypt a user's files. This feature allows CryptoMix to function offline with no need for network communication.
Recommendation: Ransomware is a continually evolving threat. It is paramount to have a comprehensive and tested backup solution in place. In the unfortunate case a reproducible backup is not in place, make sure to check for a decryptor before considering payment; avoid payment at all costs. Ransomware should be reported to law enforcement agencies who are doing their best to track these actors and prevent ransom from being a profitable business for cyber criminals.
Tags: Ransomware, CryptoMix variant, Shark
Equifax Suffered a Hack Almost Five Months Earlier That the Date It Disclosed (September 19, 2017)
The U.S.-based credit bureau, "Equifax," has confirmed that another data breach, excluding the breach that took place from mid-May to July, took place in March 2017. Equifax hired the security firm "Mandiant" to investigate the March incident, and it may be possible that firm believed that the breach had been mitigated, only to be called back in late July. Equifax has stated that the two breaches are unrelated.
Recommendation: This incident portrays the potential dangers of using security question answers that can be found in open sources such as social media accounts. In this sense, these forms are questions are flawed because information such as an individual's first car, or high school mascot for example, can often be found in social media accounts. Furthermore, accounts that rely solely on a four-digit PIN as a password are as secure as the amount of numbers used.
Tags: Data breach, Equifax
PyPI Python Repository Hit by Typosquatting Sneak Attack (September 19, 2017)
Researchers have discovered that threat actors have engaged in a new form of typosquatting that targets users of Python programming language packages from the official Python Package Index (PyPI) repository. Unknown actors were able to hide malicious code inside of 10 packages for Python 2.x by typosquatting filenames. For example, "urllib3-1.21.1.tar.gz" was impersonated as "urllib-1.21.1.tar.gz," and other fake packages appeared as "acquisition" impersonated as "acqusition." Researchers note that the fake packages contain the same code as the authentic ones, however, the installation script contains malicious but somewhat benign code.
Recommendation: It is important that your company institute policies regarding what can be downloaded on work machines, and downloads should only be allowed if they are absolutely needed. Furthermore, security researchers note that if outbound connections are found leading to 121[.]42[.]217[.]44 on port 8080, it may indicate that a fake package was downloaded. Reinstalling the legitimate package should mitigate the issue. Furthermore, machines can be checked for fake packages by running the following "pip list --format=legacy | egrep '^(acqusition|apidev-coop|bzip|crypt|django-server|pwd|setup-tools|telnet|urlib3|urllib) '". If any package is listed remove using "pip uninstall " and installing the correct package instead.
Tags: Typosquatting, PyPI
Does Your Mobile Anti-Virus App Protect or Infect You? (September 18, 2017)
The Android anti-virus application, "DU Antivirus Security Ð Applock & Privacy Guard," has been found to collect information from a device without the user's consent, according to Check Point researchers. Researchers state that when the application runs on a device for the first time it collects data from the device that consists of call logs, contact lists, unique identifiers and possibly the device location. The information is encrypted and then to a remote server. The data is then used if an individual uses another application create by DU group called "Caller ID & Call Block - DU Caller." Google has since removed the malicious application, and DU has released a new version that does not include the data collection feature.
Recommendation: Always keep your mobile phone fully patched with the latest security updates. Use the Google Play Store / Apple App Store to obtain your software, and avoid downloading applications, even if they appear legitimate, from third-party stores. In addition, it is important to review the permission the application will request, and comments from others who have downloaded the application may also be useful. Furthermore, it is paramount that mobile devices be kept up-to-date with the latest security patches and employ trusted antivirus software.
Tags: Mobile, Android, Data theft
Malspam Pushing Trickbot (September 18, 2017)
Researchers have discovered a new malspam campaign in which actors are distributing emails that purport to be from "National Westminster Bank" (NatWest). The message claims that an incoming payment cannot be completed because there are errors in the recipient's account information. The email then points to document file attachment to check the payment details. The attachment uses NatWest's logo in an attempt to trick the recipient into enable macros. If they are enabled, the recipient will be infected with the "Trickbot" trojan.
Recommendation: All employees should be educated on the risks of malspam and how to identify such attempts. Poor grammar and urgent content are often indicators of these type of attacks. Additionally, messages that request a recipient to open a file attachment should also be avoided.
Tags: Malspam, Trojan, Trickbot
Observed Threats
This section includes the top threats observed from the Anomali Community user base as well as sensors deployed by Anomali Labs. A ThreatStream account is required to view this section. Click here to request a trial.
TrickBot Tool Tip
TrickBot is a modular Bot/Loader malware family which is primarily focused on harvesting banking credentials. It shares heavy code, targeting, and configuration data similarities with Dyreza. It was first observed in September 2016 and both the core bot and modules continue to be actively developed. Both x86 and x64 payloads exist. It has been distributed using traditional malvertising and phishing methods. Flashpoint recently (2017-07-19) observed TrickBot operators leveraging the NECURS Botnet for distribution. Previously, Anomali Labs released a Threat Bulletin detailing the unpacking of this malware family.
Tags: TrickBot, Family-Trickbot, victim-Financial-Services
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



