Threat Intelligence Feeds
In today’s digital world, cyberthreats evolve daily. From phishing scams to ransomware, organizations need more than firewalls — they need foresight. That’s where threat intelligence feeds come into play. These real-time data streams empower cybersecurity teams to identify and stop threats before they strike.
Staying ahead of cyber adversaries requires speed, precision, and context. Threat intelligence feeds provide the raw materials security teams need to act quickly and confidently when faced with an attack — or better yet, to stop one before it starts.
What Is a Threat Intelligence Feed?
A threat intelligence feed is a flow of threat data. It delivers essential information on emerging and active cyberthreats, including:
- Malicious IP addresses and URLs
- Malware hashes and file signatures
- Indicators of compromise (IoCs)
- Zero-day vulnerabilities
- Threat actor behavior and tactics, techniques, and procedures (TTPs)
These feeds are a core component of modern threat intelligence strategies.
Why Are Threat Intelligence Feeds Important?
Threat intelligence feeds assist organizations in remaining proactive regarding their cybersecurity efforts. They give teams the ability to prioritize, detect, and respond to malicious activity more effectively.
Here’s why they matter:
- Early detection: Spot threats before they cause damage
- Automation: Integrate with security information and event management (SIEM), firewalls, and endpoint detection and response (EDR) tools
- Improved response: Reduce incident response times
- Threat landscape awareness: Stay ahead of new attack methods
Types of Cyberthreat Intelligence Feeds
Different types of threat intelligence data serve different purposes. The main types include:
- Strategic intelligence: High-level trends for decision-makers
- Tactical intelligence: Info about attack methods and tools
- Operational intelligence: Ongoing threat campaigns and actor behavior
- Technical intelligence: Real-time IoCs that suggest an attack is underway
Where Are Threat Intelligence Feeds Sourced From?
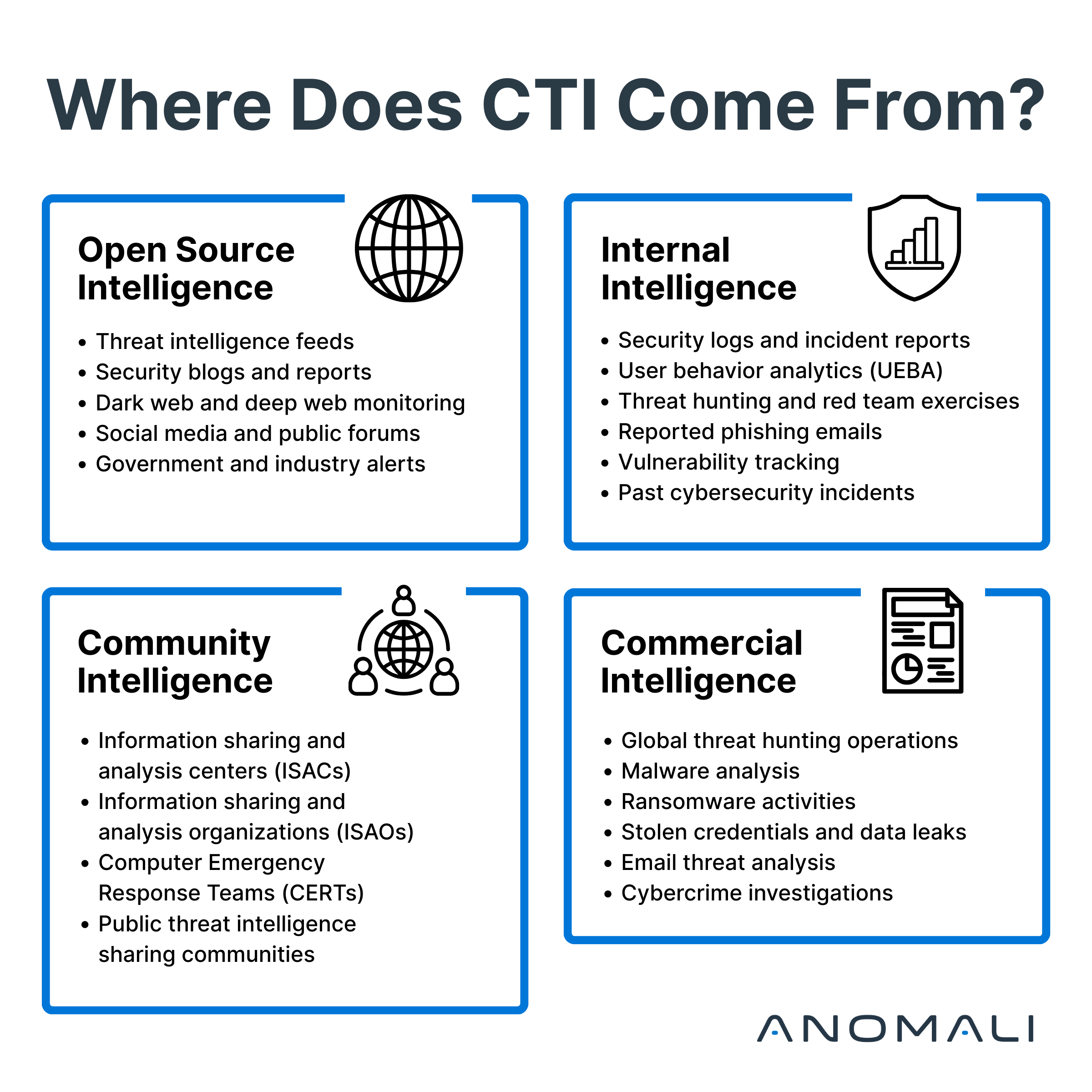
Threat intelligence can be gathered from a wide range of sources, broadly separated into four main categories:
- Open source intelligence (OSINT) feeds: Free, community-driven, and widely accessible
- Commercial threat intelligence feeds: Paid feeds offering advanced analysis and industry-specific data
- Internal threat intelligence: Data generated from your own organization’s logs, alerts, and past incidents
- Community intelligence: Shared intelligence through collaborative efforts among cybersecurity professionals and organizations (ISACs and ISAOs)
How Threat Intelligence Feeds Work
Threat intelligence feeds are most valuable when integrated into security infrastructure, such as:
- Firewalls and intrusion detection systems (IDS)
- SIEM tools
- EDR platforms
- Threat hunting and forensics
- Patch management and vulnerability prioritization
Integration enables automated threat detection and response, allowing security teams to focus their time and energy on the most critical alerts.
Benefits of Using Threat Intelligence Feeds
CTI teams use threat intelligence to strengthen their security posture in a number of ways, including:
- Real-time protection from known threats
- Reduced risk exposure and downtime
- Faster, data-driven decision-making
- Improved compliance and audit readiness
Challenges to Consider
While powerful, threat feeds also come with challenges:
- Data overload and false positives
- Integration complexity
- Lack of context for raw data
- Timeliness — stale data can lead to blind spots
Best Practices for Using Threat Intelligence Feeds
Cybersecurity teams can get the most from threat feeds by following these best practices:
- Choose high-quality, reputable feeds (commercial and open source): Regularly assess provider reliability and relevance.
- Regularly review and tune your integrations: Ensure feeds are aligned with current infrastructure and threat models.
- Combine external and internal intelligence: Leverage both perspectives for more comprehensive coverage.
- Use automation to reduce manual workloads: Free up analyst time and streamline response.
- Keep your threat data updated and contextualized: Stale or decontextualized data can create blind spots.
- Correlate with business context: Ensure threat data is enriched with information about your organization’s assets, users, and risks.
Key Takeaways
Threat intelligence feeds are a critical asset in any cybersecurity toolkit. They turn raw threat data into actionable insights, helping organizations defend against evolving threats quickly and precisely.
With the right feeds and proper integration, your security team can move from reactive to proactive cybersecurity, stopping threats before they start.
How Anomali Aggregates Threat Intelligence Feeds
Anomali sets the standard for integrating and analyzing threat intelligence feeds:
- The Anomali Security and IT Operations Platform includes Anomali ThreatStream, which leverages the industry’s largest curated threat repository to detect threats faster and with more context.
- ThreatStream’s AI and large language model (LLM)-powered analysis correlates internal telemetry with external feeds in real time.
- The platform integrates seamlessly with SIEM, extended detection and response (XDR), security orchestration and automated response (SOAR), and threat intelligence platforms (TIP), supporting unified workflows.
- Agentless, cloud-native design offers cost-effective scale, visibility, and long-term data retention for historical lookback.
Ready to integrate threat intelligence feeds and elevate your security operations? Schedule a demo.