More From This author
Free Threat Intel Consolidated at COVID-19 Attacks Resource Center
Free Threat Intel Consolidated at COVID-19 Attacks Resource Center

Blog
Free Threat Intel Consolidated at COVID-19 Attacks Resource Center
Anomali Presents the Black Hat 2019 Travel Guide
Anomali Presents the Black Hat 2019 Travel Guide

Blog
Anomali Presents the Black Hat 2019 Travel Guide
Anomali at RSA Conference 2019 - Better than Ever
Anomali at RSA Conference 2019 - Better than Ever

Blog
Anomali at RSA Conference 2019 - Better than Ever
Detect ‘18 - Who’d Ya Call? Threatbusters!
Detect ‘18 - Who’d Ya Call? Threatbusters!

Blog
Detect ‘18 - Who’d Ya Call? Threatbusters!
Anomali Announces New Threat Platform and SDKs at Detect '18
Anomali Announces New Threat Platform and SDKs at Detect '18

Blog
Anomali Announces New Threat Platform and SDKs at Detect '18
Verizon Launches Threat Intelligence Platform Service in Partnership with Anomali
Verizon Launches Threat Intelligence Platform Service in Partnership with Anomali

Blog
Verizon Launches Threat Intelligence Platform Service in Partnership with Anomali
Anomali Raises $40 Million in Series D Funding
Anomali Raises $40 Million in Series D Funding

Blog
Anomali Raises $40 Million in Series D Funding
FTSE 100 Report: Targeted Brand Attacks and Mass Credential Exposures
FTSE 100 Report: Targeted Brand Attacks and Mass Credential Exposures

Blog
FTSE 100 Report: Targeted Brand Attacks and Mass Credential Exposures
10 Reasons to be Thankful for a Security Analyst
10 Reasons to be Thankful for a Security Analyst

Blog
10 Reasons to be Thankful for a Security Analyst
Anomali Provides Threat-Sharing Expertise Before Congress
Anomali Provides Threat-Sharing Expertise Before Congress

Blog
Anomali Provides Threat-Sharing Expertise Before Congress
NCSAM – Dialing in on Cybersecurity Education
NCSAM – Dialing in on Cybersecurity Education

Blog
NCSAM – Dialing in on Cybersecurity Education
A Closer Look at the German Election
A Closer Look at the German Election

Blog
A Closer Look at the German Election
Improve Security Through People in Four Simple Steps
Improve Security Through People in Four Simple Steps

Blog
Improve Security Through People in Four Simple Steps
Anomali Limo – Take the Fast Lane to Threat Intelligence
Anomali Limo – Take the Fast Lane to Threat Intelligence
Blog
Anomali Limo – Take the Fast Lane to Threat Intelligence
6 Ways to Help Improve your Security Posture
6 Ways to Help Improve your Security Posture

Blog
6 Ways to Help Improve your Security Posture
Anomali Forum – Your Cyber War Room
Anomali Forum – Your Cyber War Room
Blog
Anomali Forum – Your Cyber War Room
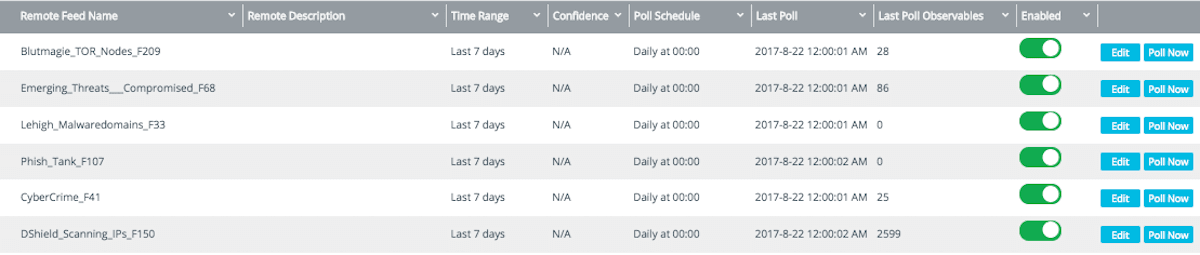
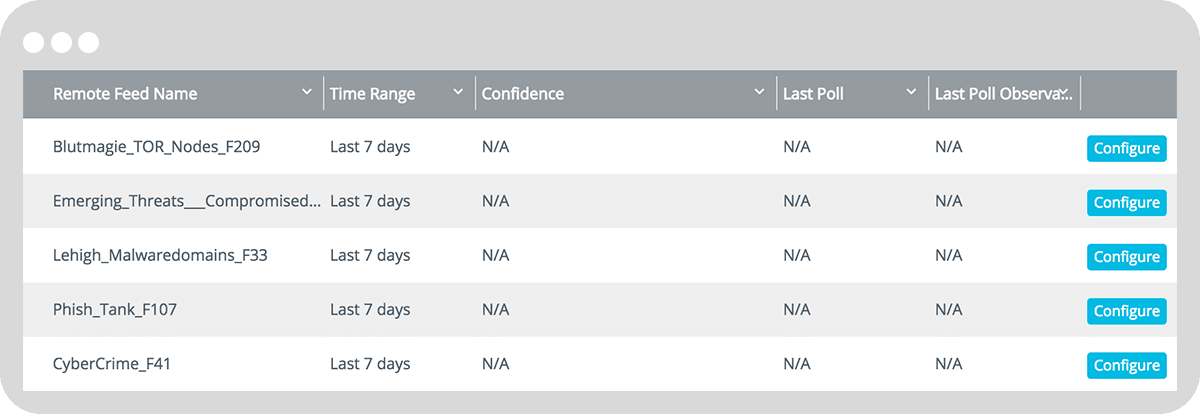
Anomali Limo – Free Intelligence Feeds
Anomali Limo – Free Intelligence Feeds
Blog
Anomali Limo – Free Intelligence Feeds
Targeted vs Indiscriminate Attacks
Targeted vs Indiscriminate Attacks
Blog
Targeted vs Indiscriminate Attacks
Anomali Begins Education Outreach Initiative
Anomali Begins Education Outreach Initiative

Blog
Anomali Begins Education Outreach Initiative
Global Elections, Global Problems
Global Elections, Global Problems

Blog
Global Elections, Global Problems
Ransomware – A Tech or Human Problem?
Ransomware – A Tech or Human Problem?

Blog
Ransomware – A Tech or Human Problem?
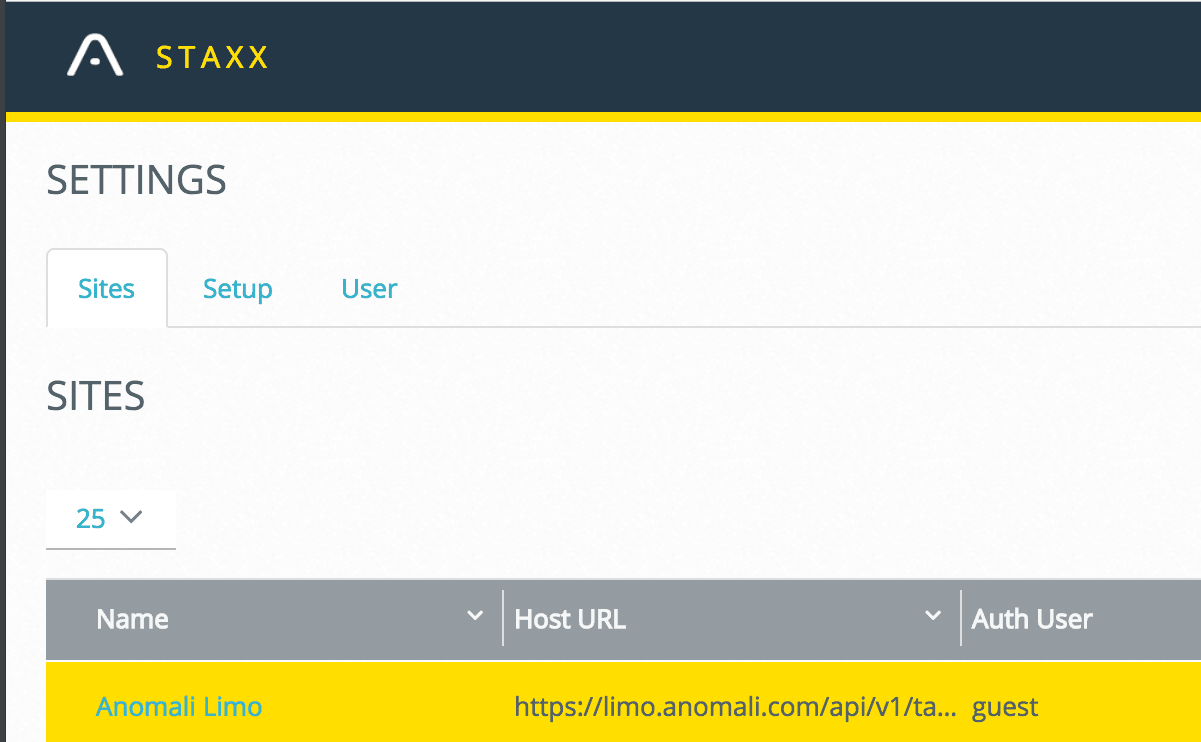
STAXX 2.3 is Here - Features New Anomali Limo Service
STAXX 2.3 is Here - Features New Anomali Limo Service
Blog
STAXX 2.3 is Here - Features New Anomali Limo Service
Maximizing the Potential of Open Source Threat Intelligence Feeds
Maximizing the Potential of Open Source Threat Intelligence Feeds

Blog
Maximizing the Potential of Open Source Threat Intelligence Feeds
STIX/TAXII: All Your Questions Answered
STIX/TAXII: All Your Questions Answered

Blog
STIX/TAXII: All Your Questions Answered
Why Brand Monitoring is a Security Issue - Compromised Credentials
Why Brand Monitoring is a Security Issue - Compromised Credentials

Blog
Why Brand Monitoring is a Security Issue - Compromised Credentials
Why Brand Monitoring is a Security Issue - Typosquatting
Why Brand Monitoring is a Security Issue - Typosquatting

Blog
Why Brand Monitoring is a Security Issue - Typosquatting
Ways to Maintain your Cybersecurity Infrastructure
Ways to Maintain your Cybersecurity Infrastructure
.png)
Blog
Ways to Maintain your Cybersecurity Infrastructure
Doing Threat Intel the Hard Way - Part 6: Threat Intelligence Maintenance
Doing Threat Intel the Hard Way - Part 6: Threat Intelligence Maintenance

Blog