Resources
Resource Center
Browse our library of upcoming and on-demand webinars, brochures and datasheets, industry reports and white papers, case studies, and more.
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.


Case Study
Anomali Helps the Centers for Medicare & Medicaid Services Reduce Third-Party Risk
The Centers for Medicare & Medicaid Services (CMS) is the single largest payer for healthcare in the United States. CMS adopted an Anomali solution to gather and share threat intelligence throughout its organization effectively.


Case Study
Anomali Solves SIEM for a Global Financial Markets Infrastructure Provider
The customer, a global financial information company, had a core requirement to centralize threat intelligence while being able to support a broad range of premium third-party feeds, which meant integration was a critical security enabler.

Case Study
Anomali Empowers State Governments Against Threat Actors
State governments need to track different threat actors targeting their network and share intelligence quickly and efficiently to defend against cyberattacks. The state cybersecurity operations team quickly realized it needed to massively improve its ability to share and operationalize threat intelligence across a platform because different threats hit different departments and the team did not have enough time or resources to properly pursue those threats.


Case Study
Educational Institution Schools Threats with Anomali
To defend against cyberattacks, this public university deployed dozens of disparate software and hardware technologies ranging from basic firewalls to honeypots. Included in the mix are education and awareness programs along with IT and staff support augmentation.


Partner Datasheet
Cribl + Anomali: Solution Brief
Accelerate business productivity, prevent threats, and achieve analytics speed and scale with Cribl and Anomali. Together, Cribl and Anomali provide a comprehensive solution for processing machine data (including logs, instrumentation data, application data, security data, and metrics).


Datasheet
Take Down Service Datasheet
Anyone who has pursued takedowns will know that this can often be a complex and time-consuming process. The Anomali TakeDown service takes care of all this complexity and removes the time overhead, allowing your security teams to get on with protecting your business and organization.

Datasheet
Anomali Copilot Datasheet
Artificial Intelligence as an enabling technology has had a pervasive impact across nearly every industry that depends on technology, and nowhere is this more evident than with cybersecurity. Anomali Copilot enables immediate prioritized security responses based on detected threats, enhancing the speed and efficiency of incident response from cybersecurity analysts.

Datasheet
Anomali Intelligence Channels Datasheet
Through its rich analysis and taxonomy, the Anomali Phishing and Fraud Intelligence Channel powered by Bayse provides comprehensive phishing and fraud indicators with key contextual information, allowing customers to
protect, detect, and respond against threats.


Guide
Top 10 Cybersecurity Trends and What to Do About Them
The 2024 cybersecurity arena is a kaleidoscope of shifting threats and innovations. As hackers and defenders engage in a high-stakes digital chess match, organizations must navigate a minefield of new vulnerabilities and emerging technologies. "Top 10 Cybersecurity Trends: What To Do About Them in 2024" offers crucial insights to help you navigate this dynamic environment.


Guide
AI in Cybersecurity: Building Smart Defenses and Outsmarting Threats
If there were such a thing as a cybersecurity Swiss Army Knife, it would definitely be AI. From providing superior protection against attacks to streamlining threat hunting, AI has become the cornerstone of modern cybersecurity.


Guide
SIEM in Flux: Progressive CIOs and CISOs Are Seeing the Forest Through the Trees and Changing the Game
Insightful CIOs and CISOs recognize that it’s time to abandon outdated paradigms and adopt an entirely new approach — one that will energize their teams and help them better advise management. They know that it’s time to Be Different.


Guide
Cyber Threat Intelligence Programs: What’s Needed to Keep Up? | ESG Research & Anomali eBook
ESG Research shares how cybersecurity professionals are approaching today's threats with their cyber threat intelligence programs. The survey highlights the pervasiveness of cyber threat intelligence programs, but it also reveals how tactical they continue to be.


Guide
Mighty Guides: 7 Experts on Enhancing Your Security Defenses by Focusing on Your Adversaries
In this Mighty Guides eBook, you'll hear from seven security experts and learn why it’s essential to know your adversary and how to proactively detect active attacks and predict an adversary’s next steps.


Guide
Cybersecurity Insights 2022 - A Vertical Look
In our inaugural Cybersecurity Insights Report, we identified and explored the challenges enterprises face in establishing and maintaining a resilient cybersecurity posture, and what is needed to protect and respond to the advanced cyber threats of today and tomorrow. Now we offer a vertical perspective. Click to learn more.


Guide
COVID-19: The Global Health Pandemic and Cybersecurity Challenge – The Harris Poll Survey Results
The global pandemic has imposed many changes to our security environments. Anomali can help you keep up with the ever-changing threat landscape, including detecting and responding to targeted attacks.


Guide
Manuskript zur Verwaltung von Threat Intelligence
Lassen Sie sich von Threat Intelligence und der Implementierung einer Threat Intelligence-Lösung zur Verbesserung Ihrer Cybersicherheitsstrategie nicht beirren. Mit einem soliden Plan kann die Umstellung auf Threat Intelligence reibungslos, sinnvoll und aufschlussreich sein.


Guide
Manual de Gestión de inteligencia contra amenazas
Entender la inteligencia contra amenazas e implementar una solución de inteligencia contra amenazas para mejorar su estrategia de seguridad informática no debería ser un proceso intimidante. Con la ayuda de un plan sólido, su transición a la inteligencia contra amenazas puede ser fluida, conveniente y esclarecedora.


Guide
Playbook Gerenciamento da inteligência contra ameaças
Compreender a inteligência contra ameaças e implementar uma solução para aprimorar sua estratégia de segurança cibernética não deve ser um processo intimidador. Com um plano sólido, sua transição para a inteligência contra ameaças pode ser fácil, útil e perspicaz.


Guide
Guida alla gestione di Threat Intelligence
Comprendere la Threat Intelligence e adottare una serie di misure volte a migliorare la tua strategia di sicurezza informatica non dovrebbe essere un processo che intimorisce. Con una pianificazione solida e adeguata, la transizione verso la Threat Intelligence può essere semplice, utile e ricca di spunti interessanti.


Video
Anomali: Resilience Starts Here
Anomali delivers intelligence-driven solutions with extended detection and response (XDR) capabilities that provide relevant intelligence, precision attack detection, and the ability to effectively respond to stop breaches and attackers. Watch this video to learn how.


Webinar
Modernizing Security Operations for an AI-Driven Threat Landscape
Modernizing Security Operations for an AI-Driven Threat Landscape is a virtual webinar that explores how organizations can strengthen their security strategies in response to rapidly evolving AI-powered cyber threats. The session will highlight the challenges of legacy security systems, the growing need for real-time threat detection, and how a unified, intelligence-driven platform can enhance visibility, accelerate investigations, and improve overall resilience. Attendees will gain practical insights from industry experts on building modern, efficient security operations that deliver measurable outcomes


Webinar
Uncovering the Full Threat Landscape: Powering Up Security with a Unified Threat Intelligence & SIEM Platform
In this webinar, David Voss, Manager of Americas Solution Engineering at Anomali, explores how a unified approach across a SIEM and TIP will enhance an organization’s security posture.


Webinar
Executing the Security Mission: Takeaways from the SANS 2024 CTI Survey Results
Escalating geopolitical instability over the previous year has increased pressure on Cyber Threat Intelligence (CTI) professionals to heighten their defense strategies and provide actionable intelligence to their stakeholders.In this on-demand webcast, Steven Benton, VP of Anomali’s Threat Research and former CSO for BT Group, shares his reactions to the results of the SANS CTI 2024 Survey, which examined the challenges CTI professionals face in 2024 and how they are responding.










































































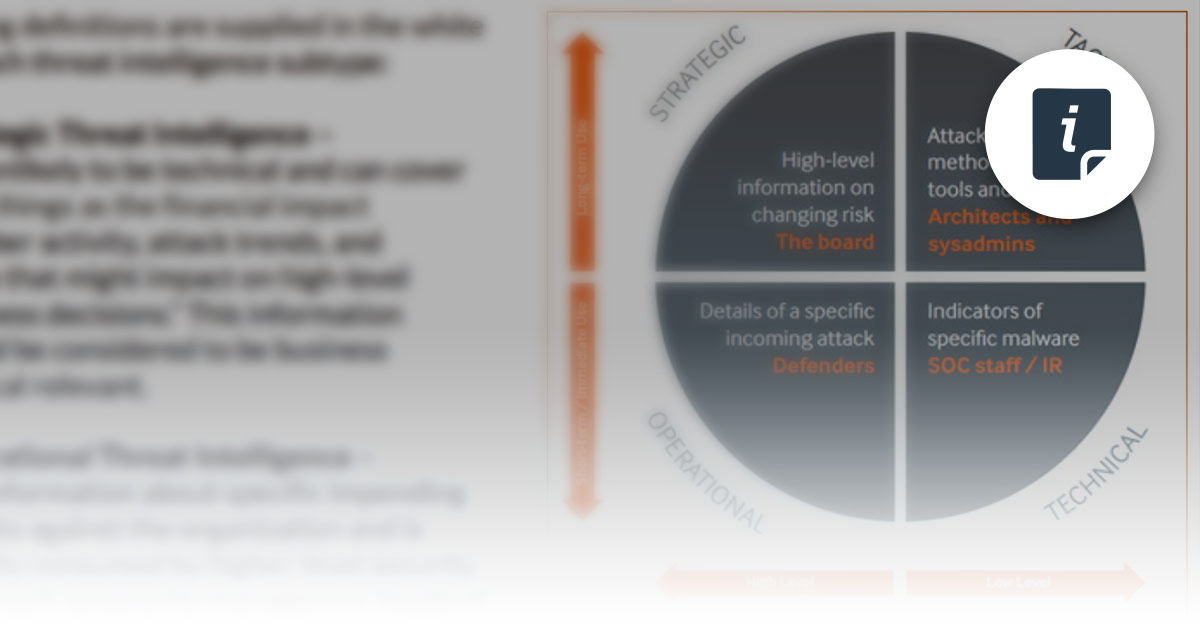


.jpeg)



















.jpeg)